Biography
I am currently Head of Digital Lab - Cyber and Security Solutions at Leonardo S.p.A.
Prior to this, I worked as Head of Cyber Electromagnetic Warfare Research at Cy4Gate S.p.A.
Before, I worked as Senior Security Researcher at Technology Innovation Institute, and as Security Researcher at Consorzio Nazionale Interuniversitario per le Telecomunicazioni.
During my Bachelor’s thesis, advised by Prof. Gennaro Boggia, I came up with a lightweight key agreement protocol for constrained IoT devices in IEEE 802.15.4e networks by adopting the Elliptic Curve Diffie Hellman protocol and the implicit certificates ECQV.
During my Master’s thesis, advised by Prof. Luigi Alfredo Grieco, I designed and implemented a security framework for Intelligent Transport Systems in Horizon 2020 BONVOYAGE project by leveraging the Attribute Based Encryption.
My Ph.D, advised by Prof. Roberto Di Pietro, allowed me to design and developing of (i) a dead-reckoning system that leverages the jamming signal to estimate the UAV position; (ii) a privacy-preserving, distributed, and lightweight solution for co-location detection and collision avoidance of autonomous UAVs, and (iii) an anonymous remote identification system for UAVs to allow them to broadcast RemoteID-compliant messages using ephemeral pseudonyms.
My research journey allowed me to publish 40+ scientific papers (journals and conferences), 12 proof-of-concepts, and 3 patents - 1080+ citations, h-index:18.
- Unmanned Aerial Vehicles Security
- Maritime Security
- Wireless Security
- Privacy Preserving Systems
- Applied Cryptography
- Internet of Things
- Cyber-Physical Systems Security
Ph.D in Computer Science and Engineering, 2021
Hamad Bin Khalifa University, Doha, Qatar
MSc in Computer Science and Engineering (cum laude), 2017
Politecnico di Bari, Bari, Italy
BSc in Computer Science, and Automation Engineering, 2014
Politecnico di Bari, Bari, Italy
Skills
Experience
Latest News
Featured Publications
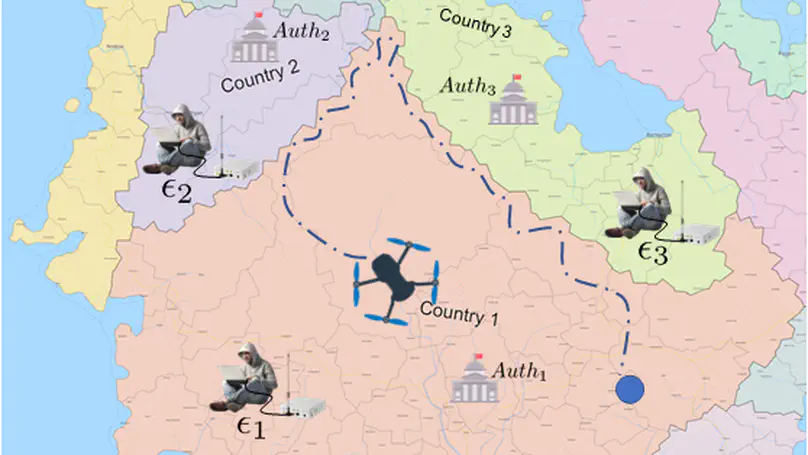
Remote Identification (RID) regulations recently promulgated worldwide are forcing commercial drones to broadcast wirelessly the location of the pilot in plaintext. However, in many real-world use cases, the plaintext availability of such information leads to privacy issues, allowing the extraction of sensitive information about the pilot and confidential details about the drone’s business. To address this issue, this paper proposes SNELL, a RID-compliant solution for selective authenticated pilot location disclosure. Using SNELL, a drone can disclose RID messages providing encrypted information about the pilot’s location. At the same time, thanks to the smart integration of Ciphertext-Policy Attribute-Based Encryption (CP-ABE) techniques, the data about the pilot location can be decrypted only by receivers with a set of attributes satisfying an access control policy chosen by the drone at run-time. Thanks to an extensive experimental assessment carried out on a real medium-end drone (Lumenier QAV-R) and a constrained chip (ESP32), we demonstrate that SNELL can fulfil all the requirements imposed by RID and relevant standardization authorities in terms of pilot location update time and message size while also requiring negligible energy toll on RID-compliant drones.
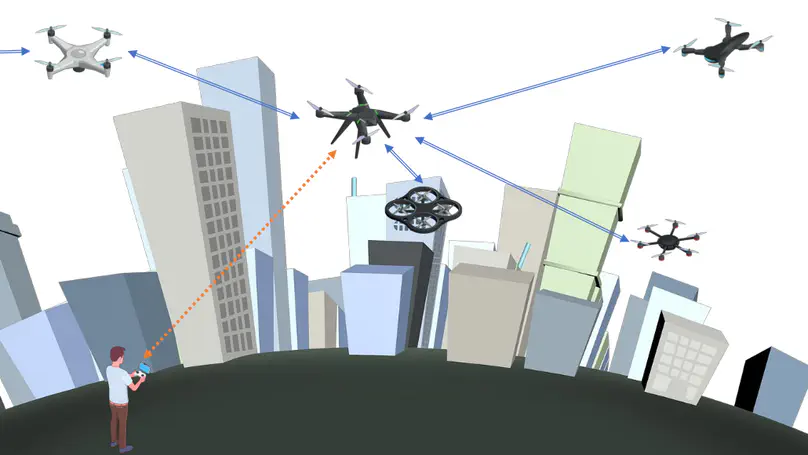
Discovering mutual proximity and avoiding collisions is one of the most critical services needed by the next generation of Unmanned Aerial Vehicles (UAVs). However, currently available solutions either rely on sharing mutual locations, neglecting the location privacy of involved parties, or are applicable for fully autonomous vehicles only—leaving unaddressed Remotely-Piloted UAVs’ safety needs. Alternatively, proximity can be discovered by adding sensing capabilities. However, in addition to the cost of the sensors, the complexity of integration, and the toll on the energy budget, the effectiveness of such solutions is usually limited by short detection ranges, making them hardly useful in high-mobility scenarios. In this paper, we propose LPPD (an acronym for Lightweight Privacy-preserving Proximity Discovery), a unique solution for privacy-preserving proximity discovery among remotely piloted UAVs based on the exchange of wireless messages. LPPD integrates two main building blocks: (i) a custom space tessellation technique based on randomized spheres; and, (ii) a lightweight cryptographic primitive for private-set intersection. Another feature enjoyed by LPPD is that it does not require online third parties. LPPD is rooted in sound theoretical results and is supported by an experimental assessment performed on a real drone. In particular, experimental results show that LPPD achieves 100% proximity discovery while taking only 39.66 milliseconds in the most lightweight configuration and draining only the 5 · 10− 6% of the UAV’s battery capacity. In addition, LPPD’s security properties are formally verified.
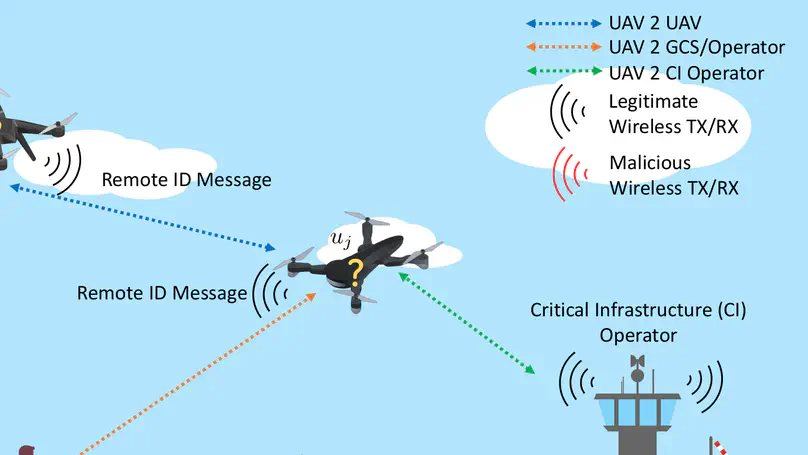
The Federal Aviation Administration (FAA) recently introduced a new standard, namely, remote identification, to improve accountability for unmanned aerial vehicles (UAVs) operations. This rule requires UAV operators to broadcast messages revealing sensitive data, such as identity and location on the wireless channel. However, this leads to security and privacy concerns among UAV operators. Unauthorized parties may easily discover the location and identity of a UAV flying in a specific area and launch attacks on it such as using wireless jamming or tracking its activity. This review investigates and systematizes the main weaknesses affecting the Remote ID capability required of modern UAVs, and the approaches through which attackers can exploit these weaknesses to disrupt safety and accountability. Moreover, this article analyzes current solutions that mitigate privacy issues associated with Remote ID. Finally, we identify multiple challenges that require to be addressed by both industry and academia, and we propose future research directions to improve the security and privacy of UAVs.
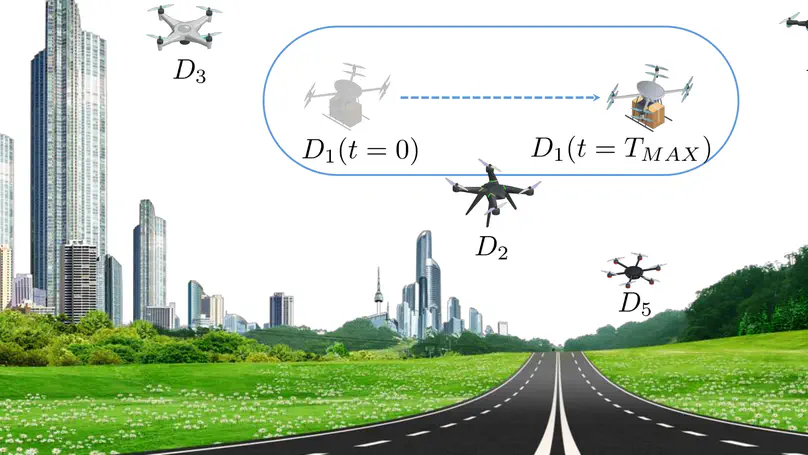
Current collision avoidance techniques deployed on Unmanned Aerial Vehicles (UAVs) rely on short-range sensors, such as proximity sensors, cameras, and microphones. Unfortunately, their efficiency is significantly limited in several situations; for instance, when a remote UAV approaches at high velocity, or when the surrounding environment is impaired (e.g., fog, noise). In the cited cases, to avoid collisions and maintain self-separation, UAVs often rely on the indiscriminate broadcast of their location. Therefore, an adversary could easily identify the location of the UAV and attack it, e.g., by physically shutting it down, launching wireless jamming attacks, or continuing tracking its movements. To address the above-introduced threats, in this article we present PPCA, a lightweight, distributed, and privacy-preserving scheme to avoid collisions among UAVs. Our solution, based on an ingenious tessellation of the space, is accompanied by a thorough analytical model and is supported by an extensive experimental campaign performed on a real 3DR-Solo drone. The achieved results are striking: PPCA can efficiently and effectively avoid collisions among UAVs, by requiring a limited bandwidth and computational overhead (84.85% less than traditional privacy-preserving proximity testing approaches), while providing unique benefits in terms of privacy of the participating UAVs.
Publications
Patents
Licenses and Certifications
- Advanced Remotely Piloted Aircraft System, Sanad Academy
- Cryptography I, Coursera
- Introduction to cybersecurity I, Cisco Networking Academy
- End-User: Social Engineering, Cybrary
- Cisco CCNA Networking for Home and Small Businesses, Cisco
- Microsoft IC3 (Internet and Computing Core Certification) - Computing Fundamentals - Key Applications - Living Online - Database Applications, Microsoft
Academic Services
Invited Speaker
- Politecnico di Bari - Seminar 2025 - Hack Is in the Air: Breaking Boundaries of Wireless Communications
- Commissione Automazione e Domotica dell’Ordine degli Ingegneri di Roma 2024 - Industrial IoT: Security and Privacy in IT/OT Integration
- ITASEC ‘23: Security and Privacy Issues in the Age of Drones
- Apulia CyberSecurity Forum 2022
Journal Editor
- Guest Associate Editor in Security, Privacy and Authentication. Frontiers in Communications and Networks Security, Privacy and Authentication - Security and Privacy for Underwater, Aerial and Ground Vehicles
General Chair
- 1st Workshop on Security and Privacy of Mobile IoT (SP-MIoT) in conj. with ESORICS 2022
Technical (Program) Committee
- 8th International Workshop on Wireless Sensors & Drones in IoT Conference Wi-DroIT 2026
- IEEE 22nd Annual International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT 2026)
- IEEE European Symposium on Security and Privacy (IEEE Euro S&P) 2026
- International Conference on Information Systems Security and Privacy (ICISSP) 2026
- IEEE 9th Cyber Security in Networking Conference (CSNet 2025)
- IEEE Annual Congress on Artificial Intelligence of Things (IEEE AIoT) 2025
- EAI SecureComm 2025
- 7th International Workshop on Wireless Sensors & Drones in IoT Conference Wi-DroIT 2025
- International Conference on Computer Communications and Networks 2025
- IEEE 21st Annual International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT 2025)
- 34th International Conference on Computer Communications and Networks (ICCCN 2025)
- 18th International Conference on Network and System Security (NSS 2024)
- IEEE Journal on Selected Areas in Communications (JSAC) - Special Issue on Zero Trust for Next-Generation Networking 2024
- EAI SecureComm 2024
- 3rd Workshop on Security and Privacy in Connected Embedded Systems (SPICES 2024) Co-located with EWSN 2024
- 6th International Workshop on Wireless Sensors and Drones in Internet of Things 2024 (Wi-DroIT 2024, co-located with DCOSS 2024)
- IEEE Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT) 2024
- Annual Computer Security Applications Conference Artifacts Evaluation (ACSAC AE) 2023
- European Symposium on Research in Computer Security (ESORICS) 2023
- IEEE GlobeCom 2023 Workshop - CelUAVSatCom
- 2nd Workshop on Security and Privacy in Connected Embedded Systems (SPICES) in conj. with EWSN 2023
- 5th International Workshop on Wireless Sensors and Drones in Internet of Things 2023 (Wi-DroIT 2023)
- International Conference on Mobility, Sensing and Networking (MSN 2022)
- Unconventional Security for Wireless Communications (USWC) in conj. with EWSN 22
- SECRYPT 2022
- ICT for Rural Development (IC-ICTRuDev) 2021
- Wireless Days 2021 - 12th Wireless Days Conference
Reviewer
- 8th International Workshop on Wireless Sensors & Drones in IoT Conference Wi-DroIT 2026
- IEEE 22nd Annual International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT 2026)
- IEEE European Symposium on Security and Privacy (IEEE Euro S&P) 2026
- International Conference on Information Systems Security and Privacy (ICISSP) 2026
- IEEE 9th Cyber Security in Networking Conference (CSNet 2025)
- IEEE Annual Congress on Artificial Intelligence of Things (IEEE AIoT) 2025
- EAI SecureComm 2025
- 7th International Workshop on Wireless Sensors & Drones in IoT Conference Wi-DroIT 2025
- International Conference on Computer Communications and Networks 2025
- IEEE 21st Annual International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT 2025)
- 34th International Conference on Computer Communications and Networks (ICCCN 2025)
- 18th International Conference on Network and System Security (NSS 2024)
- IEEE Journal on Selected Areas in Communications (JSAC) - Special Issue on Zero Trust for Next-Generation Networking 2024
- EAI SecureComm 2024
- IEEE International Conference on Computer Communications (INFOCOM) 2024
- IEEE Wireless Communications and Networking Conference (WCNC) 2024
- Annual Computer Security Applications Conference (ACSAC) 2023
- European Symposium on Research in Computer Security (ESORICS) 2023
- IEEE Transactions on Dependable and Secure Computing
- IEEE Transactions on Mobile Computing
- IEEE Transactions on Wireless Communications
- IEEE Transactions on Aerospace and Electronic Systems
- IEEE Communications Magazine
- IEEE Internet of Things Journal
- IEEE Access
- IEEE International Conference on Intelligent Robots and Systems (IROS)
- IEEE International Conference on Computer Communication (INFOCOM)
- IEEE International Conference on Communications (ICC)
- ACM Conference on Security and Privacy in Wireless and Mobile Networks (WISEC)
- European Symposium on Research in Computer Security (ESORICS) 2022
- Transactions on Emerging Telecommunications Technologies
- Elsevier Computer Communications (COMCOM)
- Elsevier Computer Networks (COMNET)
- Elsevier Pervasive and Mobile Computing
- Elsevier Vehicular Communications
- Pervasive and Mobile Computing
- International Journal of Information Security
- Journal of Computer Security
- IET Information Security
- Security and Communication Networks
Mentor for more than 20 Master and Bachelor students worldwide